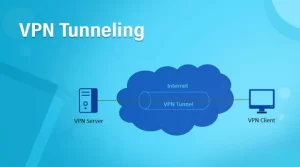
VPNs are popular tools that help users maintain online privacy, security, and anonymity. They do so by routing a user’s data through a secure, encrypted path established between their device and the remote VPN server. This act of routing your data through a secure path is called a VPN tunnel, and the secure, encrypted path is called a VPN tunnel.
VPN tunnels play a crucial role in the working of a VPN and in maintaining your privacy and security. This article provides a thorough understanding of what a VPN tunnel is, how it works, and its value in maintaining privacy and security.
What is a VPN Tunnel?
As mentioned above, a VPN tunnel is a secure pathway that a VPN uses to send your data to its destination securely instead of letting it travel on the open internet. This pathway is created between your device and a remote VPN server as soon as you connect to a VPN. The tunnel is encrypted and thus protects your data from snoopers, hackers, ISP and even surveillance agencies.
A VPN’s core functionality is through a VPN tunnel. The term “tunnel” is used as it helps data travel safely from one end to the other through a protected route. As a result, your IP address, browsing activity, and online communication all remain private and secure.
VPN providers use different tunneling protocols such as OpenVPN, WireGuard, etc. These communication protocols allow data to move across the network.
How does tunneling work?
A VPN tunnel’s main job is to see if your data is being securely protected and transmitted across the public internet. When active, it routes all the data to follow a secure path through a VPN server instead of a direct open internet connection.
When you connect to a VPN, your device sends a request to your VPN server to form a secure connection. The server verifies the request and forms a tunnel between the server and your device to allow your data to securely pass through. Whenever any data leaves your device, it travels through the tunnel to its destination.
What is the process of VPN Tunneling?
In simple terms, the VPN tunneling process sounds very basic, while in reality, it is a step-by-step process. This process starts as soon as you connect to the VPN and ends only after the VPN session is terminated. Here is all that is happening during tunneling:
- Initiating the VPN Connection: This step starts when you launch your VPN app, choose a server, and connect to it. The app begins to form a connection with the VPN service and reaches out to the server, preparing to form a link.
- Authentication and handshake: Your device and VPN server verify and authenticate each other’s identity using credentials or digital certificates. Once the authentication process is completed, a cryptographic handshake forms. The device and the VPN server decide on encryption parameters and exchange secure session keys.
- Formation of the encrypted tunnel: Once the required authentication is completed, the VPN creates a secure tunnel using protocols like WireGuard or OpenVPN. The tunnel is a secure, encrypted pathway for your data to travel.
- Data encryption and transmission: Before sending out data, your device encrypts it to prevent snooping or hacking.
- Data decryption: the VPN server receives data in an encrypted form and decrypts it using the previously agreed-upon keys to send it to the desired destination. At this stage, the server also replaces your real IP address with its own, efficiently masking your IP address and location.
- Return of data: The website sends your data back to the VPN server, which encrypts it again and sends it back to your device using the same encrypted tunnel. Your device decrypts the data, so the website loads normally on your device.
- Tunnel disintegration: Once you disconnect the VPN, the tunnel tears down and wipes the session keys, not leaving behind a trace of your encrypted session.
Why is a VPN Tunnel important for privacy and security?
In layman’s terms, a VPN tunnel is important for your privacy because it’s the encrypted pathway that carries your encrypted data securely to keep it safe and private. It not only secures your connection but also maintains online anonymity. Here is everything a VPN tunnel does:
- It encrypted your traffic through strong encryption protocols. These protocols scramble your data, making it unreadable to hackers, ISPs and other snooping third parties. In other words, it protects your data from hacks, thefts, and unwanted surveillance.
- The tunnel also helps mask your IP address and location, preventing anyone trying to snoop from knowing your location or identity.
- A VPN tunnel protects your online activity from snoopers, hackers, and network operators from monitoring.
- By masking your IP and encrypting traffic, VPN tunnels prevent advertisers and ISPs from tracking and recording your online behavior. This protects you from unwanted advertisements.
- Since a VPN tunnel hides your activity from snooping, it also helps bypass ISP throttling issues.
- VPN tunnels secure your connection, allowing you to use the internet safely on public Wi-Fi networks.
These use cases make VPN tunnels an important and core part of VPNs and your online privacy.
What are the different types of VPN Tunneling protocols?
VPN tunnels depend on tunneling protocols to establish and secure the connection between your device and the VPN server. Each protocol defines how a VPN tunnels, encrypts, and transmits your data. Since no single protocol is perfect for every situation, they vary in terms of security, speed, stability, and device compatibility.
Below are the most commonly used VPN tunneling protocols:
- OpenVPN: One of the most widely trusted VPN protocols, OpenVPN is open-source and uses strong SSL/TLS encryption. It works across almost all platforms, including Windows, macOS, Linux, Android, and iOS. Its flexibility allows it to run over both UDP and TCP, making it reliable for bypassing firewalls while maintaining high security.
- WireGuard: A modern VPN protocol built for speed and simplicity. WireGuard uses advanced cryptography and a lightweight codebase, resulting in faster connections and improved performance. It is efficient and secure, which makes it popular for both desktop and mobile VPN use.
- L2TP/IPsec: This protocol combines L2TP for tunneling and IPsec for encryption. Although it is an older technology and relatively slower in contrast to other protocols, it is still widely supported and fairly secure.
- IKEv2/IPsec: Known for stability and quick reconnections, IKEv2/IPsec performs especially well on mobile devices that frequently switch networks. It offers strong security and reliable performance, though it may not match WireGuard’s speed.
- SSTP: Developed by Microsoft, SSTP uses SSL/TLS encryption and integrates seamlessly with Windows systems. It can bypass basic firewalls but offers limited cross-platform support.
- PPTP: An outdated protocol that is fast but insecure. Due to weak encryption, it is no longer recommended for privacy-focused users.
Choosing the right VPN protocol directly affects how secure, fast, and private your VPN tunnel is.
Role of Encryption in VPN Tunneling
Encryption is the core security mechanism that gives a VPN tunnel its true privacy value. It works by converting readable data into an encoded format that can only be accessed with the correct decryption key.
When a VPN connection is established, your device and the VPN server securely exchange encryption keys and agree on the encryption standard to use. From that moment on, every piece of data traveling through the VPN tunnel is encrypted before it leaves your device.
This ensures that even if your internet traffic is intercepted, the information remains unreadable and useless to them. Modern VPN services rely on strong encryption algorithms, such as AES with 256-bit keys, which are so far known to be unbreakable.
Encryption also helps maintain data integrity by detecting attempts to alter information in transit. Without encryption, a VPN tunnel would offer little more than basic traffic rerouting. By combining tunneling with secure encryption, VPNs ensure that sensitive data, login credentials, and online activity remain confidential and protected throughout the entire connection.
Understanding split tunneling- what is it and how does it work?

When you connect to a VPN from your device, you essentially encrypt all your traffic through it. However, at certain times, you might not want your traffic encrypted, and that is where VPN Split tunneling comes in.
Split tunneling is a feature that lets you choose which parts of your traffic go through the secure VPN connection and which parts go through the regular internet connection. In simpler terms, with this feature, instead of sending all your traffic through the VPN, you can route only selected apps or websites.
VPN split tunnelling allows you to protect your sensitive activity, such as online banking, while making sure that your other traffic, such as streaming, are happening outside the VPN for better speeds. However, only a few top VPNs offer split tunneling.
Key Takeaways
A VPN tunnel provides a secure, encrypted connection that shields your online activity from hackers, ISPs, and trackers. Hiding your IP address and encrypting data through protocols like OpenVPN, WireGuard, or IKEv2, it ensures your information stays private between you and the VPN server. While using a VPN may slightly reduce internet speed, the enhanced online privacy and data protection make it worthwhile.
Selecting a reliable VPN provider is crucial to prevent logging or misuse of your data. Overall, a properly configured VPN tunnel is one of the most effective tools to maintain online privacy, secure sensitive information, and browse the internet safely in today’s digital world.
FAQ
How does a VPN help with privacy?
A VPN encrypts your internet traffic and hides your real IP, keeping your online activity private from hackers, ISPs, and trackers.
What is the value of a VPN?
VPNs secure data, mask your identity, and prevent online tracking, rendering them essential for privacy and safe browsing.
What are the benefits of using a VPN tunnel?
VPN tunnels protect data, hide IPs, secure public Wi-Fi, bypass geo-restrictions, and prevent ISP throttling.
What is the disadvantage of a VPN?
VPNs may slow connections and require trust in the provider, as logging or weak security can compromise privacy.
Is VPN 100% untraceable?
No. VPNs enhance privacy but don’t make you fully anonymous; providers or advanced tracking can still trace activity.
How much does a VPN cost per month?
VPNs typically cost around $10/month, with cheaper rates for long-term plans; free VPNs often have limits.
What are the main reasons for using a VPN?
VPNs secure data, hide IPs, unblock content, and protect public Wi-Fi; businesses also use them for safe remote access.
Can a VPN really hide my IP address?
Yes. A VPN masks your real IP with the server’s address, keeping your location and identity private online.
Is using a VPN tunnel legal?
VPNs are legal in most countries, but some nations like China, Russia, and the UAE heavily restrict or ban them.
Can you be tracked if you use a VPN?
A VPN blocks most tracking, but cookies, fingerprints, or provider logs may still reveal activity.
How can you test if a VPN tunnel is working?
Check your IP before and after connecting and run DNS/WebRTC leak tests to confirm the VPN tunnel is secure.