 Why trust VPN Guider
Why trust VPN Guider
In [year], as online safety regulations and communication standards continue to evolve, selecting the best VPN protocols has become crucial for protecting sensitive information, such as passwords, and optimizing online experiences. VPN protocols determine how data is transmitted between your device and the VPN server, impacting both speed and security.
VPN protocols create encrypted tunnels for your online traffic, ensuring it remains secure from hackers, ISPs, and other third parties. These tunnels are designed to balance streaming speed and data security, making them essential for activities like browsing, streaming, and online transactions.
Choice of the best vpn protocol – which one to use?

The streaming protocol is strict or challenging to find, but getting the specific one that could bestow the requirements of one’s needs and fit perfectly as a protocol for video streaming is always a headache.
Even the best VPN protocol cannot provide both the speed and security to the absolute as the difference between both of them would lack the presence of the other no matter even if it is listed as the best protocol for VPN.
Why does the fluctuation of these VPN tunneling protocols exist?
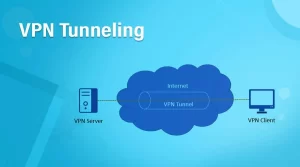
The analogy is pretty simple to decode if we consider internet security features like encryption – Every data needs to be encrypted before convening it entirely to the international internal systems and networks.
As tunneling becomes narrow, the browsing speed decreases due to the high-quality requirements of protocol for streaming and vice versa. There are multiple VPN tunneling protocols that are really helpful and speed friendly, which provide rapid protocol for streaming as the tunnels are wider, processing of routing data packets and individual sets becomes a very immaculate task.
Which is the best vpn protocol to use for streaming?
The answer isn’t that simple, depending upon the speed, security and P2P capacity of the the different protocols to choose the best VPN protocol is depending upon the recent surveys and listings according to users and developers.
Wireguard

Awarded as the fastest among the wide range of the best protocols for VPN, Wire Guard is among the top protocols as – the transfer, download and streaming of P2P files are swift compared to other competitors in the market.
WireGuard is a simple, quick, and contemporary VPN that employs cutting-edge cryptography. It attempts to be shorter, simpler, leaner, and more helpful than IPsec while avoiding the tremendous hassle. It aims to be significantly faster than OpenVPN.
WireGuard is intended to be a general-purpose VPN that can run on both embedded interfaces and supercomputers. Initially designed for the Linux kernel, it is now cross-platform (Windows, macOS, BSD, iOS, and Android) and extensively deployed. It is still in the early stages of development. Still, it has the potential to be the most secure, user-friendly, and straightforward VPN option in the business.
[postFaq]
Open VPN

Suppose we talk about the multiple aspects and advantages of Open VPN being one of the best VPN protocols for being among protocols for streaming. In that case, it is entirely free from hasty subscriptions and paywalls, making its secure access across intermediate platforms sharing features cherry on top of already packed OpenVPN supremacy.
Open VPN has been standardized in the industry for its definite balance between security, functionality, reliability, ability to bypass firewalls and many more, making it a marker of grade among the best VPN protocols.
Because OpenVPN supplies a client, it cannot access anything independently. It would be best if you utilised your own or third-party servers. Only when coupled with dependable servers, can OpenVPN overcome geo-restrictions and provide access to any streaming platform.
Another alternative is to use the free OpenVPN community servers. However, if you want to use the VPN for streaming, remember that these servers cannot guarantee access to geo-blocked material. Furthermore, no one can vouch for their security, which means your identity may be revealed to the applications and websites you use.
Point-to-Point Tunneling Protocol
One of the well-known VPN tunneling protocols, Point-to-Point tunneling Protocol, a.k.a PPTP, might be an old version compared to the current new generation protocols. However, it is well known and is still a standard version of implementation when it comes to VPN services, due to its antique nature and the absence of development in the recent past, PPTP fails to guarantee a secure and safe tunneling option via its TCP control channel.
Its complicated functionality gives it a quality unlike any other routing or tunneling facility, keeping it in contention for the best VPN protocol on the market.
PPTP uses a Generic Routing Encapsulation tunnel to enclose Private Point to point Protocol packets, which can also be found in multiple modern-day VPNs used for geoblocking credentials and masking.
Hence, PPTP is the modern initiator of VPNs and other protocols for streaming.
On the TCP port, 1723 Communication to the peer initiates a PPTP tunnel. This TCP connection is then used to establish and manage the same peer’s GRE tunnel. The GRE tunnel is used to transport encapsulated PPP packets, allowing the tunneling of any protocol that can be transported over PPP, such as IP, NetBEUI, and IPX.
The PPTP GRE packet structure is non-standard, with a new acknowledgement number field replacing the conventional routing field in the GRE header. Those modified GRE packets, however, are directly wrapped into IP packets and viewed as IP protocol number 47, just as they are in a standard GRE connection.
IPSec
IPsec is a suite of the best VPN protocol that work together to provide encrypted communications between devices. It contributes to the security of data exchanged over public networks. IPsec is a popular best VPN protocol that operates by encrypting IP packets and authenticating the source of the packets.
“IPsec” stands for “Internet Protocol” and “sec” stands for “secure.” The Internet Protocol is the primary routing protocol used on the Internet; it uses IP addresses to determine where data will flow. IPsec adds encryption* and authentication to this procedure, making it more secure.
[postVpn]
Layer Two Tunneling Protocol
Extending of the Point-to-Point Tunneling Protocol (PPTP) – L2TP is that internet service providers (ISPs) employ to create virtual private networks (VPNs). L2TP must use an encryption protocol to transfer data within the tunnel to maintain security and privacy.
Most L2 data types may be sent using L2TP across an IP or Layer Three (L3) network. The procedure starts a tunnel across the internet between an L2TP access concentrator (LAC) and an L2TP network server (LNS). This allows for the encapsulation and transmission of a Point-to-Point Protocol (PPP) connection layer across the internet.


